Choose an option below to explore the documentation for the latest user interface (UI) or the classic UI.
A view permission is the right to see a resource and any child resources of that resource. View permissions determine which users can see and work with which resources.
You assign a view permission to users or user groups on either a domain or community level.
Note If you limit the view permissions on a domain in a community, you can no longer update the view permissions on the community level.
Only these assigned users can see those resources and their child resources, including the assets. View permissions also impact asset relations, so if you don't have view permissions for an asset, you also don't see the relations that contain that asset, for example in views or on the asset page of the related assets.
Example If User A has view permissions for Community 4 but not Community 6, then User A is able to see and work with any resources in Community 4, including the assets. Anything in Community 6 is inaccessible to User A, unless they are subsequently assigned view permissions for Community 6.
Understanding view permissions
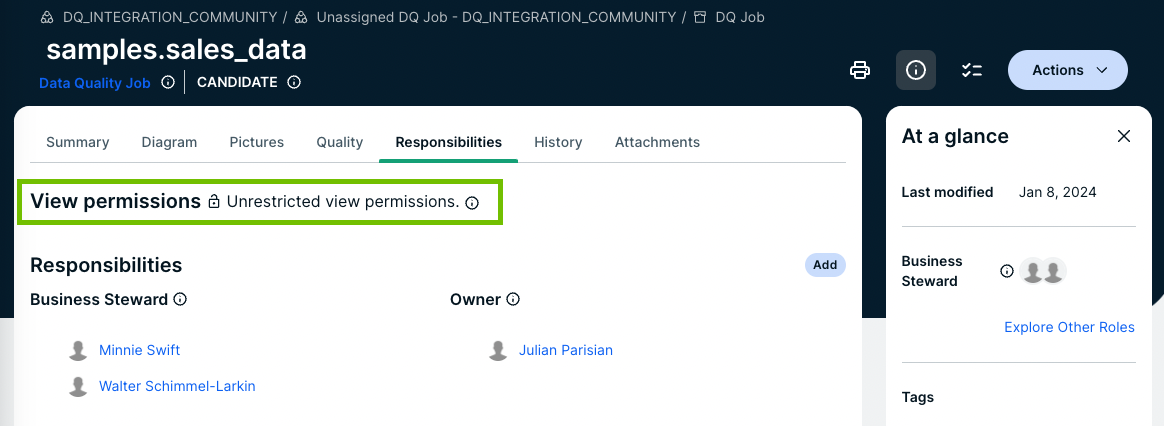
By default, all users can see all resources. If there are no view permissions, the View permissions section of the Responsibilities page of that resource shows Unrestricted view permissions.
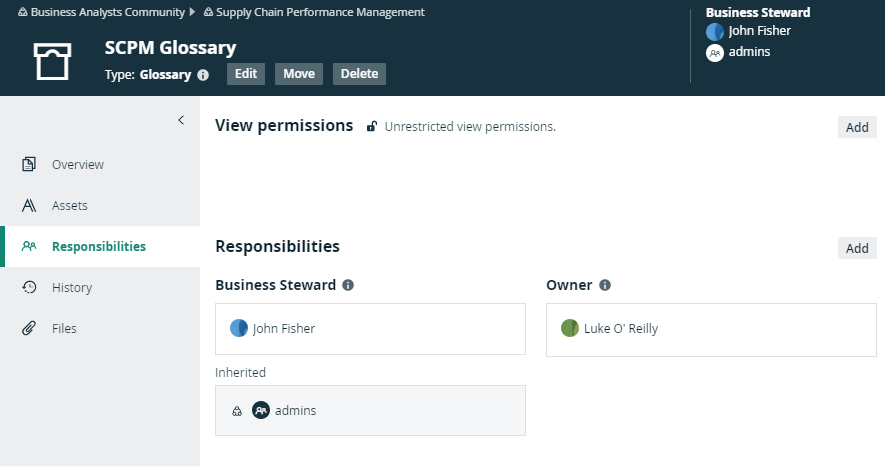
If you add users or user groups to the view permissions of a resource, only those users or groups can view the resource and its child resources.
All child resources inherit the view permissions from parent resources. Once you have added users or user groups to the view permissions of a resource, you cannot create view permissions for any of its child or parent resources.
You can recognize inherited view permissions by their gray background.
- A user that has a role with the System Administration global permission, for example the Sysadmin global role, can see all views in Collibra, even if they are not shared.
- A user with the Manage all views permission can see only views that are shared.
Impact of view permissions on responsibilities
View permissions affect responsibilities. If a user has a responsibility for a certain resource, but does not have view permission, that user cannot act upon that responsibility. The responsibility becomes inactive, due to the lacking view permission.
To activate the responsibility, you must create the view permission for this resource or a parent resource.
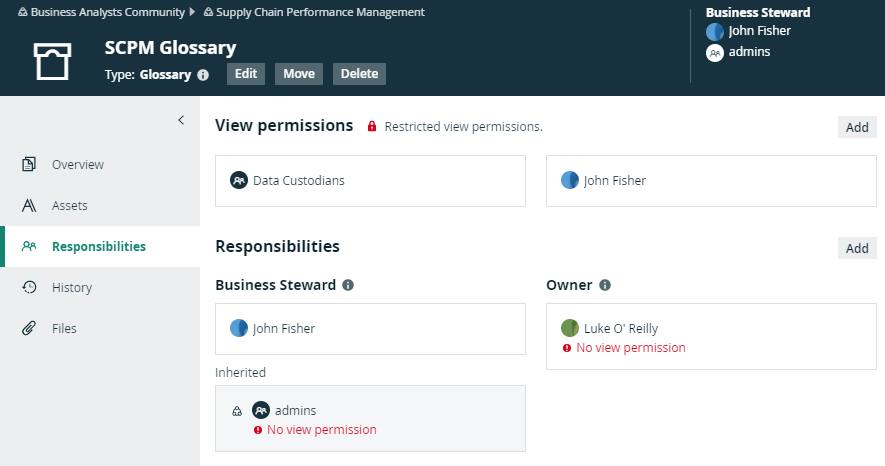
In the example below, Luke O'Reilly is the Owner of the SCPM Glossary domain, but he does not have the view permission to see the domain. As a consequence, he cannot see the assets or act on his responsibility. On the Responsibilities page, his responsibility shows an error message to clearly show that there is a problem. You can solve the problem in one of the following ways:
- Create a view permission for Luke.
- Add Luke to the user group that has a view permission.
- Delete all view permissions, so that everyone can see the assets.
- Delete Luke's responsibility as Owner and pick another person for that role.
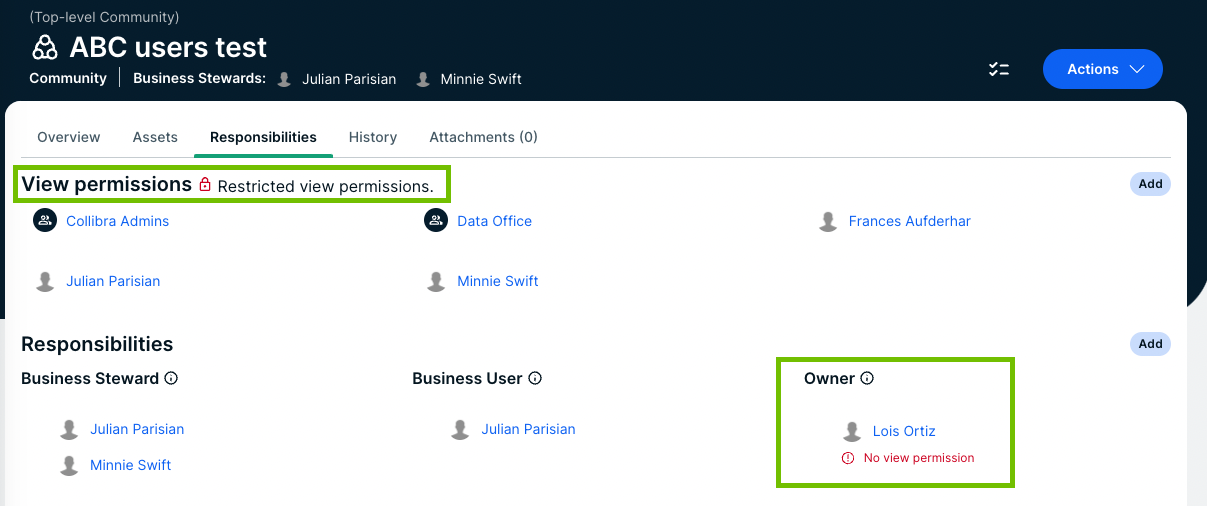
In the example below, Lois Ortiz is the Owner of the ABC users test domain, but she does not have the view permission to see the domain. As a consequence, she cannot see the assets or act on her responsibility. On the Responsibilities page, her responsibility shows an error message to clearly show that there is a problem. You can solve the problem in one of the following ways:
- Create a view permission for Lois.
- Add Lois to the user group that has a view permission.
- Delete all view permissions, so that everyone can see the assets.
- Delete Lois's responsibility as Owner and pick another person for that role.