Storing connection credentials
This topic explains the security architecture for connection credentials on Edge. Understanding this process helps you verify that your data encryption meets your organization's security standards.
Note You can manage your data source secrets and credentials by using Vaults.
Connections and capabilities credentials are stored solely on the Edge site. While at rest, credentials use envelope encryption where the credentials are encrypted by a key, which is then encrypted by another key.
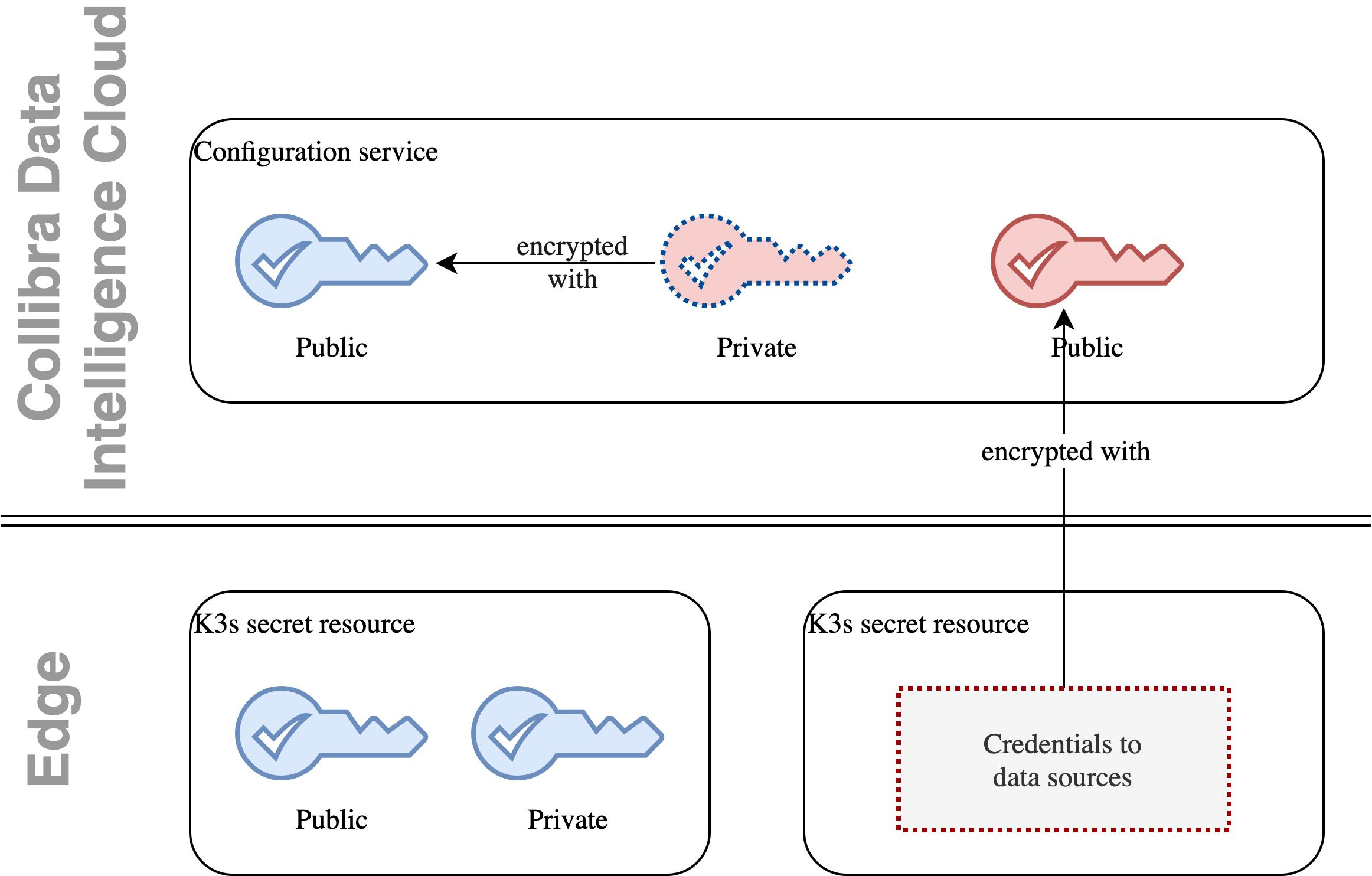
The Edge native encryption mechanism is based on two RSA key pairs. They are stored in the following places:
| Keys | Collibra Platform server | Edge server | Purpose | When is it generated? | Where is it stored? |
|---|---|---|---|---|---|
| Red public key | Yes | No | Used to encrypt connection credentials. | After the Edge site is successfully installed. | In the Collibra Cloud. |
| Red private key | Yes (encrypted using public blue key) | No | Used to decrypt connection credentials. | After the Edge site is successfully installed. | Encrypted by the Blue public key in the Collibra Cloud |
| Blue public key | Yes | Yes | Used to encrypt red private keys. | During the installation or re-installation of the Edge site. | Encrypted on the Edge site. |
| Blue private key | No | Yes | Used to decrypt red private key. | During the installation or re-installation of the Edge site. | Encrypted on the Edge site. |
The Edge site owns the blue key pair. The blue private key is stored as a Kubernetes credential on the Edge server, ensuring it undergoes native K3s encryption as described in Customer credentials. Similarly, Collibra Platform owns the red key pair.
When a capability is executed, Collibra Platform encrypts every credential on Edge with the red public key. It then encrypts the red private key with the blue public key and sends the package to the Edge site for capability execution.
Once received, the Edge site uses its blue private key to decrypt the red private key. Finally, it uses the red private key to decrypt the credentials and inject them into the capability container.
Note Inside the Kubernetes cluster, all other credentials, for example data source credentials and Datadog credentials, are stored encrypted at rest.