Collibra Console configuration options
- Settings that are indicated with an asterisk (*) are mandatory settings.
-
To edit the Console configuration, you need the ADMIN role, except for settings or sections marked with (**), which require the SUPER role. As the SUPER role does not exist for cloud environments, settings that require the SUPER role are not available in Collibra Platform environments. If you want to edit one of these settings, please create a support ticket.
1 Configuration
| Setting | Description |
|---|---|
| Base URL* (**) | The base URL to access Collibra Console. |
|
Startup timeout for Jobserver |
The duration in milliseconds before the The default value is |
|
Startup timeout for the Repository |
The duration in milliseconds before the The default value is |
|
X-Frame options |
The option to specify the content of the HTTP-header X-Frame-Options. It is set on all the rendered pages and should be used to avoid a click-jacking attack. By default, we specify that only pages from the same origin can use the rendered pages in a frame. Note Changing this options requires a reboot of the server. |
| X-Robots-Tag (**) | Using this header to restrict search engines from indexing console pages. Directives included by default: noindex, nofollow. |
| Cache-Control (**) | Using this header to control how browsers cache resources. Directives included by default: no-cache, no-store. |
| Enable service monitor |
|
| Hide super users* (**) |
|
1.1 Email configuration (**)
The configuration of email notifications. More information: Configure Collibra Console email settings.
| Setting | Description |
|---|---|
| Username | The username used to sign in to the SMTP server. |
|
Password |
The password used to sign in to the SMTP server. A password is not required. |
| From address (*) |
The email address used as the sender of all outgoing emails. See Email configuration for Collibra Platform and Collibra Console to update this setting in cloud environments. |
| Host (*) | The URL or IP address of the SMTP server. |
| Port (*) |
The port used to access the SMTP server. The default port is 25. |
| Start TLS |
|
| Sending threads (Requires restart) | The number of threads used to send emails. The default value is 1. |
| Max retries (Requires restart) | The number of retries for sending emails. The default value is 3. |
1.2 LDAP configuration
The configuration of LDAP to handle the authentication. For a tutorial about the LDAP configuration of Collibra Console, see Collibra Support Portal.
| Setting | Description | ||
|---|---|---|---|
| Enable LDAP integration (*) | Global setting to enable or disable LDAP integration. | ||
|
Enable LDAP SUPER users (**) |
Allow LDAP users to have the Collibra Console SUPER role. The default value is false, any LDAP users with SUPER role will have same access rights as ADMIN role users. |
||
| Time limit (*) |
Maximum time in milliseconds for LDAP search operations. The default value is 120,000 milliseconds or two minutes. Set it to 0 if you do not want a time limit. |
||
| Servers | This section configures one or more LDAP servers. | ||
|
When using SSL, use the LDAP's protocol and use the correct port. The SSL section in the configuration should also be configured for this. |
||
|
The main LDAP Domain Name (DN) to be able to connect to the LDAP server. This DN should be able to access all the users and groups that you want to sync. | ||
|
The password for the main LDAP DN to connect to the LDAP server. | ||
|
General base path to which all DNs are relative. As a general rule, this should stay empty for most configurations. | ||
|
The base DN where the users are located. Subtree search is used, so all DNs located below the base are searched for matching users. | ||
|
User filter to which users authenticating in Collibra Platform should comply. | ||
|
User filter to which users imported by the synchronization job should comply. This should be a subset of or equal to the Authentication user LDAP filter. When empty, the same filter will be used. as specified in the Authentication user LDAP filter. | ||
|
LDAP authentication mechanism; must be one of the following:
Note When using TLS, dont forget to configure the SSL security section. |
||
|
In case of TLS usage, if set to true, Collibra Console tries to shutdown all TLS connections. | ||
|
Specifies how referrals should be handled; must be one of:
|
||
|
The base DN where all groups are located. | ||
|
The attribute to define that users are member of a group, for example uniqueMember. This field is mandatory when mapping LDAP groups to roles. |
||
|
The LDAP filter to which each group should comply to be synced. | ||
|
The mapping of the LDAP users that are members of the group with a specified DN to a role. |
||
| User field mapping | Configuration mapping of all the user fields. Here you can configure to what LDAP field a given user field should be mapped. Leave empty if it should not be considered in the synchronization. | ||
|
Username mapping is mandatory for LDAP to be enabled. | ||
|
Role mapping is mandatory for LDAP to be enabled. This is the LDAP directory field that defines which console role the user should have. If you do not intend on using this configuration mapping use the default mapping of role. |
||
|
Email mapping is mandatory for LDAP to be enabled. | ||
| Default role |
The default role for LDAP users. The default role is READ. Only a Collibra Console SUPER user can grant the SUPER role to an LDAP user. |
1.3 UI configuration (**)
The configuration of user interface features.
| Setting | Description |
|---|---|
|
Optimize CSS This setting requires the SUPER role. |
|
|
Optimize JavaScript This setting requires the SUPER role. |
|
|
Concatenate JavaScript This setting requires the SUPER role. |
|
|
Velocity cache This setting requires the SUPER role. |
|
|
Modules JSON overrides This setting requires the SUPER role. |
DISCLAIMER: If you choose to customize any aspects of Collibra, including CSS or other modules/page-definition customizations, these must be thoroughly tested between upgrades. Customizations are unsupported and can break between upgrades. We recommend your organization and the responsible parties maintain a list of customizations applied to Collibra and use that as a checklist for validating upgrades in a test or lower environment. If changes are needed to customizations, make appropriate preparation and testing plan to promote to your production instance. |
|
Modules properties overrides This setting requires the SUPER role. |
DISCLAIMER: If you choose to customize any aspects of Collibra, including CSS or other modules/page-definition customizations, these must be thoroughly tested between upgrades. Customizations are unsupported and can break between upgrades. We recommend your organization and the responsible parties maintain a list of customizations applied to Collibra and use that as a checklist for validating upgrades in a test or lower environment. If changes are needed to customizations, make appropriate preparation and testing plan to promote to your production instance. |
|
Page definition overrides This setting requires the SUPER role. |
DISCLAIMER: If you choose to customize any aspects of Collibra, including CSS or other modules/page-definition customizations, these must be thoroughly tested between upgrades. Customizations are unsupported and can break between upgrades. We recommend your organization and the responsible parties maintain a list of customizations applied to Collibra and use that as a checklist for validating upgrades in a test or lower environment. If changes are needed to customizations, make appropriate preparation and testing plan to promote to your production instance . |
1.4 Console Export File configuration
| Setting | Description |
|---|---|
| Console Export File process timeout (*) |
The duration in milliseconds before the creation of a console export file is considered as a failure. The default value is 43,200,000 milliseconds or 12 hours. During an upgrade, this value is also taken into account. |
| Console Export File cleanup interval (Requires restart) (**) |
Interval in minutes for the cleanup of console export files. The default value is 720 minutes. |
| Console Export File compression level (**) |
The compression level for console export files. Possible values are from 0 to 9, and -1 for the Java default compression. The default value is 0. |
1.4.1 Console Export File schedule configuration
| Setting | Description |
|---|---|
| Default max retained (*) |
The default maximum number of retained console export files related to a backup schedule. 0 signifies retain all. |
1.4.2 Console Export Guardrail Alerts configuration
The configuration determines who receives email notifications and when these notifications are sent regarding approaching console export file limits. By default, all users with the ADMIN role receive these notifications.
| Setting | Description |
|---|---|
| Frequency (*) | The frequency guardrail alerts are sent out:
|
| Threshold (*) | The percentage of global export limit in use to trigger alerts. The default value is 90. |
| Opted in emails (*) | The list of email addresses that have opted in to receive export guardrail alerts. |
| Opted out emails (*) | The list of email addresses that have opted out to receive export guardrail alerts. |
1.4.3 Console Export File retry configuration (**)
| Setting | Description |
|---|---|
| Console Export File Retry attempts (*) |
The number of times an automated retry will be attempted after encountering the initial console export files error. The default value is 1. |
| Console Export File retry delay (*) |
Time in milliseconds between retry attempts. The default value is 5,000 milliseconds. |
| Console Export File retry agent check timeout (*) |
The maximum amount of time in milliseconds a retry has in order to establish agent communication before the retry will timeout. The default value is 30,000 milliseconds |
1.5 CSRF configuration
| Setting | Description |
|---|---|
| Enable CSRF protection |
If enabled, Collibra Console checks the validity of the request using a CSRF token. |
1.6 Session configuration
| Setting | Description |
|---|---|
| Idle Session timeout (Requires restart) (*) |
The duration in seconds of idle time before a Collibra Console session times out. The minimum value is 5 minutes, the maximum is 24 hours. The default value is 1,800 seconds or 30 minutes. |
1.7 Security Configuration (**)
|
Setting |
Description |
|---|---|
| User locked out interval (Requires restart) (*) | The number of seconds during which a user cannot sign in to Collibra Console after the specified number of incorrect Login attempts. |
| Login attempts (Requires restart) (*) | The number of times that a user can try to sign in to Collibra Console before being locked out for the time defined in User locked out interval. |
| Interval for consecutive login attempts (Requires restart) (*) |
The number of seconds during which the user has the amount of login attempts specified in the Login attempts field. |
1.7.a Disclaimer
-
 True: Console will display a obfuscating disclaimer dialog box after login.
True: Console will display a obfuscating disclaimer dialog box after login. -
 False: There is no disclaimer after login.
False: There is no disclaimer after login.
1.7.b Disclaimer message
The disclaimer dialog box content: text string with basic HTML tags. If not set, it displays a default message.
1.7.c User locked out interval (Requires restart) * (**)
The interval in seconds in which an user is locked out of the console, after successive failed login attempts.
The default value is 300.
1.7.d Login attempts (Requires restart) * (**)
User accounts are temporarily locked out of the console after the specified number of incorrect login attempts per interval for consecutive login attempts.
The default value is 5.
1.7.e Interval for consecutive login attempts (Requires restart) * (**)
The interval in seconds in which users can fail the number of login attempts.
The default value is 60.
1.7.f Users allowed multiple concurrent sessions (**)
A list of usernames that are allowed to have multiple concurrent sessions in the console.
1.7.1 SSO
| Setting | Description | ||
|---|---|---|---|
| Mode |
The SSO mode of Collibra Console. Collibra Console only supports SAML_ATTRIBUTES. |
||
|
When SSO is enabled, a user can still navigate to the /signin page and try to log in via that page. However, you can disable that page.
|
|||
|
Default role |
The default role for all SSO users. The default role is READ. SSO users with a SUPER role will be downgraded to users with the ADMIN role. Only a Collibra Console SUPER user can enable the SUPER role for SSO users. |
||
|
Enable SSO SUPER users(**) |
This option is only visible if you have the SUPER role. |
||
| SAML | The configuration of SAML. | ||
|
The URL of the SAML metadata file to be used. The URL always has to be reachable by the Collibra environment. | ||
|
The entity ID inside the metadata to be referenced. Note A metadata file can describe multiple entity IDs, make sure to use in the entity ID from the correct metadata file. |
||
|
By default, this URL is the same as the URL of your Collibra environment but if your IDP expects another value, you can fill it out here. Warning Make sure that the intended destination endpoint (The Destination attribute in the SAML response) matches the URL being used here. So this is only to be used in specific IDP circumstances When setting this, and getting the error "SAML message intended destination endpoint did not match recipient endpoint" check the Destination attribute in your SAML response and this parameter. |
||
|
|
||
|
|
||
|
|
||
|
Configure whether the SP authentication should set the authentication to go passive. If True, the IDP or browser MUST NOT take visibly control of the user interface. See the SAML 2.0 specification for more details. This is only relevant if Force authn is True. |
||
|
Configure the nameID used in the SP authentication. If set, the full content will be sent as a nameID. Use a fully qualified nameID. Default nameID="urn:oasis:names:tc:SAML:2.0:nameid-format:persistent". See SAML 2.0 specification for accepted nameID values. |
||
|
Map groups from the group field to a role in the Collibra Console. The Field key must be a name of a group as defined in your IDP, the Field value is one of the Collibra Console roles (READ, ADMIN, SUPER). | ||
|
The mappings of attributes in the SAML response. The values are used as keys to look for in the SAML response. | ||
|
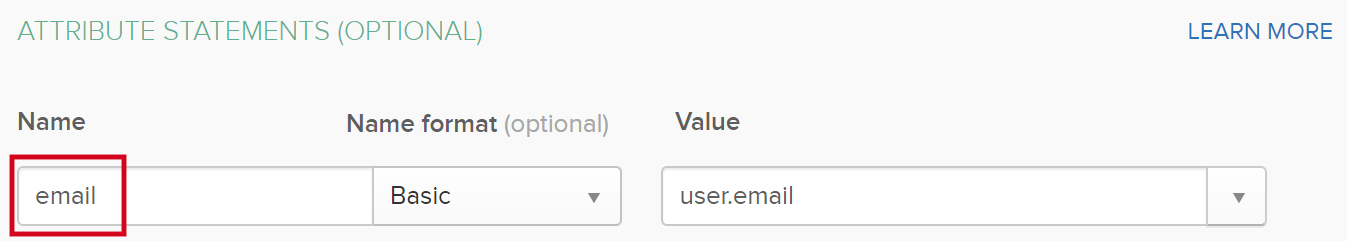
The mapping for the user's username. The value of this attribute must be the name of the SAML attribute as defined in your IDP. In the following example, the value in Collibra Console must be email. This is the used name in your IDP software, see the following screenshot.
This field is mandatory. |
||
|
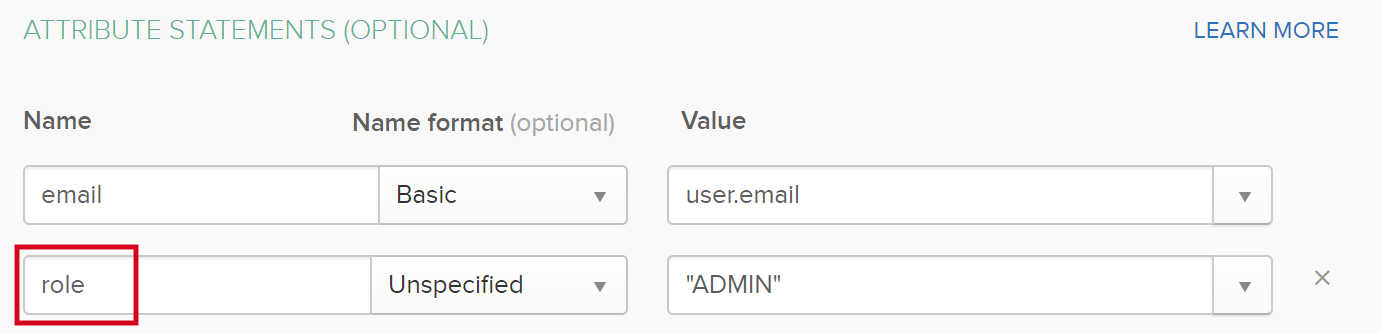
The mapping for the user roles. The value of this attribute must be the name of the SAML attribute as defined in your IDP. In the following example, the value in Collibra Console must be role. This is the used name in your IDP software, see the following screenshot.
|
||
|
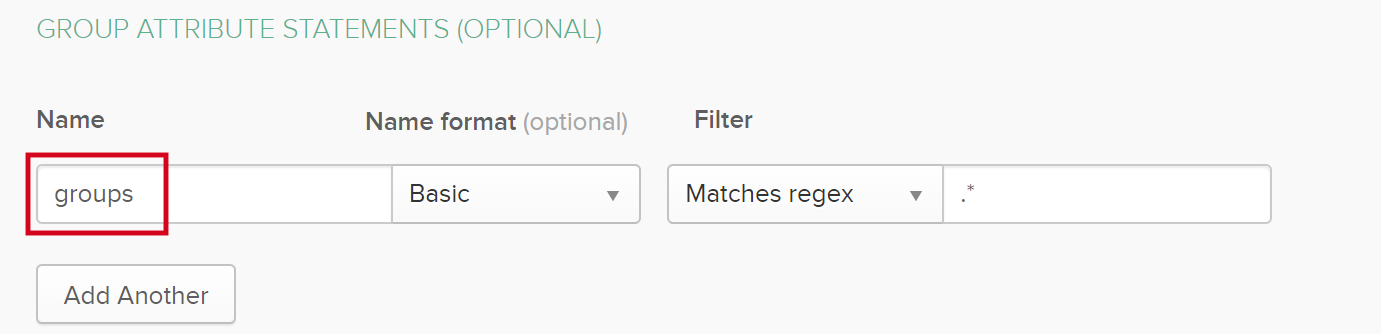
The mapping to define which attribute holds group information. The value of this attribute must be the name of the SAML attribute as defined in your IDP. In the following example, the value in Collibra Console must be groups. This is the used name in your IDP software, see the following screenshot.
If there is more than one group attribute statement, add them as comma-separated list. |
||
|
Settings for the SAML requested authentication context. The authentication context is the way in which the IDP authenticates the user. By default the authentication context will mandate user/password authentication over HTTPS. | ||
|
Disable the SAML requested authentication context. Set to True if you wish to configure the IDP to use specific authentication contexts, without the need to send one in the request. | ||
|
Specifies the comparison method used to evaluate the requested authentication context. One of: "exact", "minimum", "maximum", "better". The industry default is "exact", other options are "minimum", "maximum" and "better".
For more details, see the SAML 2.0 specification (Section 3.3.2.2.1). |
||
|
All SAML authentication classes to be sent in the SAML authentication request. Use to tune the authentication context on the IDP side. Default="urn:oasis:names:tc:SAML:2.0:ac:classes:PasswordProtectedTransport" (Which means user/password over HTTPS). For more details, see the SAML 2.0 specification (Section 3.3.2.2.1 & Section 2.7.2.2). | ||
|
All SAML authentication declarative classes to be sent in the SAML authentication request. For details, see the SAML 2.0 specification (Section 3.3.2.2.1 & Section 2.7.2.2). | ||
| Signout | The sign-out redirection settings. | ||
|
Enable this option to redirect to another page than the default sign-out page. The default page when you sign out is the Collibra Console sign-in page. | ||
|
The URL to redirect to when you sign out. |
1.7.2 HTTP headers
The configuration of the HTTP response headers of Collibra Console.
|
Field |
Description |
|---|---|
|
URL pattern |
The pattern of the URLs to which the HTTP response header is applied. This field supports wildcard characters such as Tip The following pattern matches all URLs: |
|
HTTP headers |
The HTTP response headers in a key-value format. You can add new HTTP response headers by clicking Add at the bottom of the section, and entering the HTTP response header name as the field key and the HTTP response header value as the field value. |
1.7.3. Whitelists
Add whitelist placeholders that you can use in security headers.
| Setting | Description |
|---|---|
| connect-src whitelist | The connect-src whitelist. To use this whitelist in a security header, use the {connectSrcWl} placeholder. |
| font-src whitelist | The font-src whitelist. To use this whitelist in a security header, use the {fontSrcWl} placeholder. |
| frame-src whitelist | The frame-src whitelist. To use this whitelist in a security header, use the {frameSrcWl} placeholder. |
| img-src whitelist | The img-src whitelist. To use this whitelist in a security header, use the {imgSrcWl} placeholder. |
| script-src whitelist | The script-src whitelist. To use this whitelist in a security header, use the {scriptSrcWl} placeholder. |
| style-src whitelist | The style-src whitelist. To use this whitelist in a security header, use the {styleSrcWl} placeholder. |
| frame-ancestors whitelist | The frame-ancestors whitelist. To use this whitelist in a security header, use the {frameAncestorsWl} placeholder. |
| Tableau frame-ancestors whitelist | The tableau frame-ancestors whitelist. To use this whitelist in a security header, use the {tableauFrameAncestorsWl} placeholder. |
1.7.4 Password configuration
Configure how strong a users password should be.
| Setting | Description |
|---|---|
| Minimum length * |
The minimum length for any created password. The default value is 12. |
| Maximum length * |
The maximum length for any created password. The default value is 1024. |
| Digits required |
Whether the password policy should mandate at least one digit. The default value is |
| Non alphanumeric required |
Whether the password policy should mandate at least one non-alphanumeric (Special) character. The default value is |
| Uppercase required |
Whether the password policy should mandate at least one upper-case character. The default value is |
| Lowercase required |
Whether the password policy should mandate at least one lower-case character. The default value is |
| Username disallowed |
Whether the password policy should mandate that the password isnt the same as the username. The default value is |
| Password reset link validity period |
The validity period of the password reset link in minutes. The value must be minimum 15 minutes and maximum 1440 minutes (24 hours). The default value is 60 minutes. |
1.8 Rate limiters (**)
A list of rate limiters for console REST endpoints.
| Field | Description |
|---|---|
| Endpoint URL * | The URL of the endpoint that should be rate limited. Please replace any path parameter UUID in the URL with {id}. |
| Endpoint method * | The HTTP method of the endpoint that should be rate limited. |
| Duration in minutes * | The time duration in minutes in which the requests can be made. |
| Maximum requests * | The maximum number of requests that can be made in the time window. |
| Enable rate limiter * | Whether the limiter is active. |