Warning Jobserver and all related Jobserver integrations reached their End of Life in commercial environments in October, 2024. In Collibra Platform for Government and Collibra Platform Self-Hosted environments, they will reach their End of Life on May 30, 2027.
For information on registering a data source via Edge, go to Registering and synchronizing a data source via Edge.
CyberArk is middleware to manage authentication and is used to provide access to various data sources. You can use CyberArk to let Data Catalog access and ingest data sources with username and password authentication.
- The CyberArk authentication implementation can't be used with CData drivers.
- You can only authenticate to data sources using username and password authentication.
Setting up CyberArk authentication
You set up CyberArk authentication when you register your data source or manage your JDBC driver. When you register your data source or manage your JDBC driver, you only provide the username, the password you need to authenticate to the data source is stored in CyberArk and is retrieved by the Jobserver. When you ingest a data source using CyberArk authentication, the Jobserver uses certificate-based mutual authentication to authenticate to CyberArk.
Note The connection to CyberArk is only supported over HTTPS.
To authenticate via CyberArk, you have to enable CCP WebService in CyberArk and keep the default name AIMWebService unchanged. You also have to provide your own CyberArk certificates via a JKS keystore that you upload to Collibra when you register your data source or manage your JDBC driver. The JKS keystore contains the CyberArk client certificates, the private key and, if required, a server certificate.
Tip For more information on the configuration of CyberArk certificates, see the CyberArk user guide.
Authentication workflow
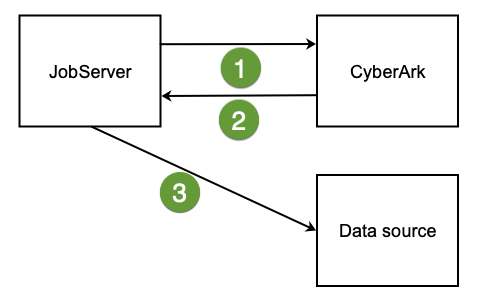
|
Step |
Action |
|---|---|
| 1 |
The Jobserver requests credentials from CyberArk through a certificate-based mutual authentication. |
| 2 |
CyberArk provides the Jobserver with a username and password. |
| 3 |
The Jobserver uses these credentials to authenticate to a data source. |
Configuration
If you want to use CyberArk authentication, you need the following connection properties.
| Label | Property |
Description |
Mandatory |
|---|---|---|---|
| Keystore file | keystoreFile |
The name of the keystore file. The keystore must contain the client key and client certificate or certificate chain. If The value must have the following format: Example |
Yes |
|
Keystore password |
keystorePass |
The password required to open the keystore. |
Yes |
|
Default truststore |
defaultTruststore |
The indication of the default truststore. The default value is set to
|
No |
| CyberArk address | cyberarkAddress |
The host and port number through which the CyberArk server is accessible. The format of the address is Example |
Yes |
|
CyberArk application ID |
cyberarkAppId |
The application ID as defined in CyberArk. This ID should be provided by your network or system administrator. |
Yes |
| CyberArk query |
cyberarkQuery |
The CyberArk query. This query should be provided by your network or system administrator. |
Yes |