Edge communicates with Collibra and third-party servers using an outbound-only model. This means that Edge perform tasks as commands over a long polling session.
- When communicating with Collibra, Edge retrieves work commands through long polling sessions.
Example When communicating with Collibra, Edge starts a session and requests a task from Collibra. If no tasks are available, the session ends, and Edge immediately starts a new session. If a task is available, Edge retrieves the task from Collibra, completes it, and sends the results back to Collibra.
- When communicating with third-party services, Edge pushes and pulls data as needed.
All data transmitted from your Edge site is encrypted using certificates issued by a Certificate Authority (CA) chosen by Collibra. The encryption uses TLS 1.3 and either basic authentication or OAuth.
- If you installed your Edge site before 2025.08 your Collibra server uses username and password authentication. It is possible to change the password of this user account by following the steps outlined in our Update Edge user password article.
- If you installed your Edge site with the 2025.08 release or later, your Collibra server uses OAuth authentication.
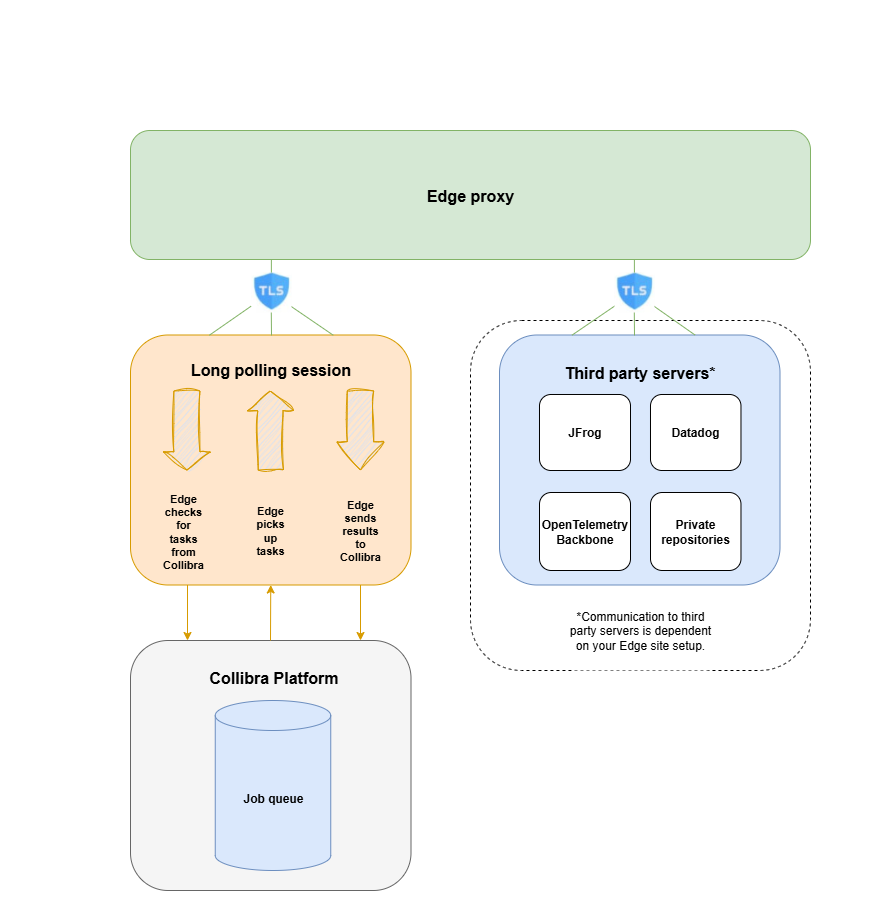
Edge communication to Collibra
- Edge sites always use REST API endpoints to establish connections.
- Edge requires access to a Collibra server. It is needed for:
- Reading a request queue, which is a queue with jobs that need to be run on Edge.
- Returning the metadata results of Edge jobs.
- Edge manages Collibra Platform and data source credentials. This has the following consequences:
- Credentials are not accessible outside of Edge.
- Credentials used on an Edge site are encrypted with a key that is secured in Collibra.
- Credentials of data sources and Collibra can be updated if necessary.
- All configuration parameters, files, or strings marked as secret, are stored on the Edge site encrypted with a public key that resides in Collibra. The private part of that key is encrypted with a public key from the Edge site. As a result, secrets can only be decrypted with both key pairs, one residing on the Edge site and the other on Collibra.
- If you are using a forward proxy with your Edge site, you must use the proxy server's CA.
Edge communication to third-party servers
Depending on your Edge site setup, Edge may need to communicate with other servers, such as JFrog, for maintenance purposes.
- JFrog: Edge communicates with JFrog via API Key Pair over HTTPS in order to download Helm Charts and Docker Images that are running on Edge.
- OpenTelemetry Backbone: Edge communicates with OpenTelemetry Backbone via HTTPS in order to upload various Edge related metrics.
- DataDog: Edge communicates with DataDog via API Key Pair over HTTPS in order to upload logs from all Edge components:
- Private repositories: If you are using a private repository for your Edge site, Edge communicates via HTTPS to communicate information from your Edge site to Collibra Platform. For more information, go to About private registries with Edge.
Note If you have any questions about data privacy and what information is sent via third party components, such as Datadog, reach out to your Collibra representative.