Security Settings lets admin users configure general and dataset security settings in Data Quality & Observability Classic.
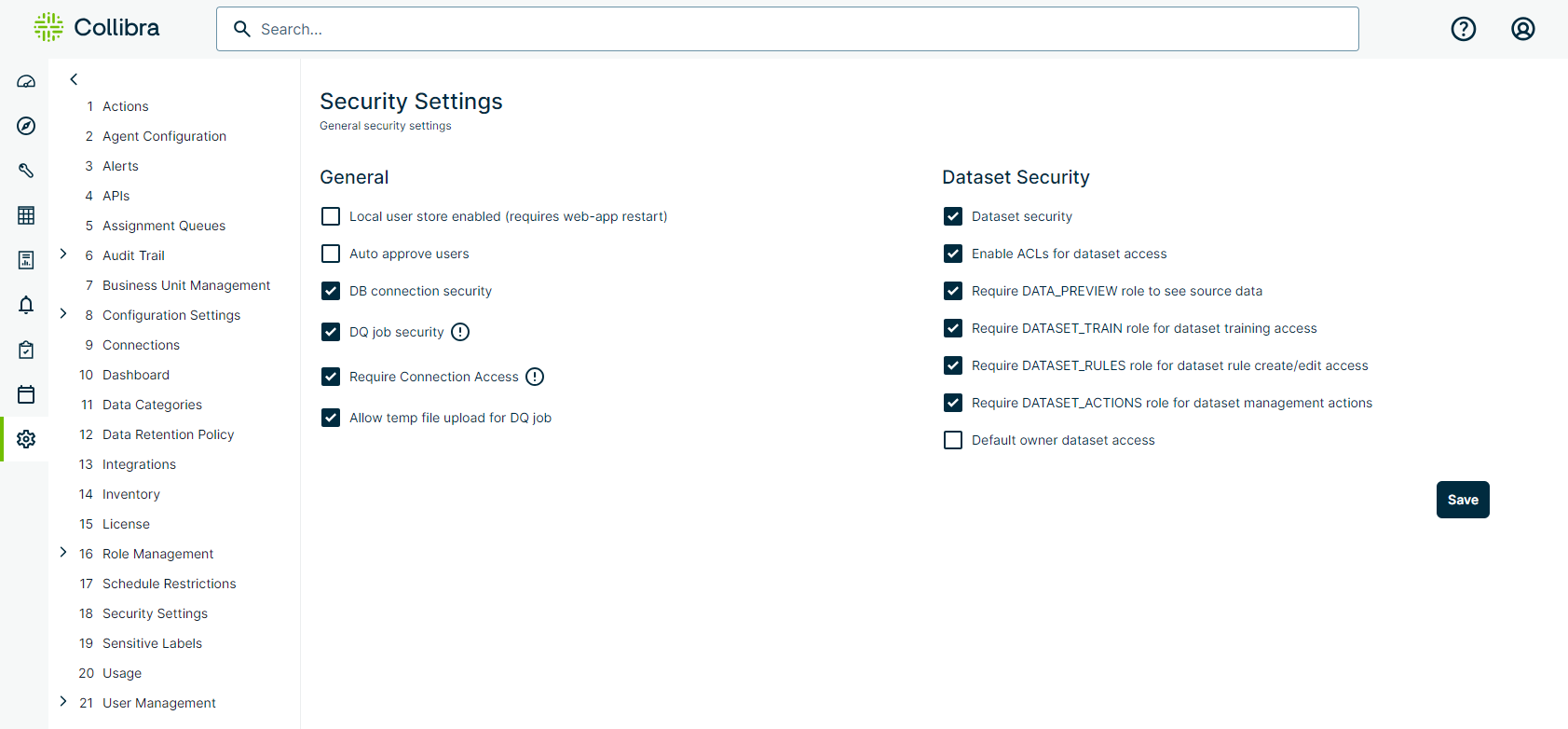
General
| Setting | Description | ||||||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Local user store enabled | Allows you to create and administer users stored in the internal Metastore. After enabling or disabling this setting, you must restart Data Quality & Observability Classic. For more information, go to Local User Store Authentication. |
||||||||||||||||
| Auto approve users |
Automatically approves local users upon sign-in. When enabled, the accounts of new users are enabled, unlocked, and have ROLE_PUBLIC automatically assigned to them. When disabled, the accounts of new users are disabled, locked, and do not have any roles assigned to them. Another user with ROLE_ADMIN, ROLE_USER_MANAGER, or ROLE_OWL_ROLE_MANAGER must grant the new user account at least one role before the new user can sign in to Data Quality & Observability Classic. |
||||||||||||||||
| DB connection security |
Allows admin users to select and map roles to connections. Note Any user with those mapped roles can see the connection in the Data Quality & Observability Classic application. |
||||||||||||||||
| DQ Job security |
Makes ROLE_OWL_CHECK a requirement for users to run DQ Jobs. Note ROLE_ADMIN and ROLE_OWL_CHECK are the only roles that can run DQ Jobs when DQ Job security is enabled. Show table
|
||||||||||||||||
| Require Connection Access | When DQ Job security and Require Connection Access are enabled, ROLE_ADMIN or ROLE_OWL_CHECK must be assigned to both the user and connection for the user to run, schedule, and create DQ Jobs on the connection. | ||||||||||||||||
| Allow temp file upload for DQ Job | Allows users to upload temporary files from their local machines to use as data sources in Explorer. | ||||||||||||||||
| Set token expiration duration |
Sets the expiration duration of the authentication token for DQ client API calls. If an API call is made and the token has reached the time limit, the API response is 401. The default setting is one hour. To change the duration, modify the following command in Copy
The time is specified in milliseconds (ms). In this example, 3600000 milliseconds=60 minutes. |
Dataset Security
| Setting | Description |
|---|---|
| Dataset security |
When enabled, if a user does not have a full permission role granting them the ability to perform specific tasks, they cannot perform them. The following list shows specific tasks that dataset security can prevent users without the correct full permission role from performing:
Note In the list above, a single role encompassing all tasks does not exist. Instead, multiple roles must be mapped to relevant datasets as full permission roles to allow users to perform all listed tasks. Users with ROLE_ADMIN or ROLE_DATASET_MANAGER can map roles to datasets as full permission roles on the Dataset Management page. |
| Enable ACLs for dataset access |
When access control list (ACL) is enabled, administrators can configure the following options to limit usage/permissions on datasets:
ACLs turn on the following access levels:
If you select Partial for a dataset, the following further permissions can be individually turned on or off:
However, the above permissions only affect a user's access/functionality unless the corresponding global security settings are also enabled:
|
| Require DATA_PREVIEW role to see source data |
When enabled, only users with ROLE_DATA_PREVIEW can preview source data on the Explorer, Findings, Profile, Rules, and Dataset Overview pages. Note When creating a job and the Require DATA_PREVIEW role to see source data setting is enabled, users without the ROLE_DATA_PREVIEW role cannot access the "Visualize" function in the Row Filter option of the Select Rows step in Explorer. |
| Require DATASET_TRAIN role for dataset training access |
When enabled, only users with ROLE_DATASET_TRAIN can train datasets, which includes the ability to adjust the scoring model, modify thresholds of Adaptive Rules, and validate, invalidate, or resolve data quality findings. |
| Require DATASET_RULES role for dataset rule create/edit access |
When enabled, only users with ROLE_DATASET_RULES can manage rules. Note ROLE_DATA_PREVIEW is also required to manage rules. |
| Require TEMPLATE_RULES role to add, edit, or delete a rule template |
When enabled, only users with ROLE_TEMPLATE_RULES or ROLE_ADMIN can manage template rules. Users without ROLE_TEMPLATE_RULES or ROLE_ADMIN can view the list of template rules, but cannot add, edit, or delete them. |
| Require DATASET_ACTIONS role for dataset management actions |
When enabled, only users with ROLE_DATASET_ACTIONS can edit jobs, rename, publish, assign data categories and business units, and enable integrations from the Dataset Manager. These permissions are also accessible by users with the ROLE_ADMIN and ROLE_DATASET_MANAGER roles. Note Users with this role can rename the dataset but not the dataset alias.
|
| Default owner dataset access | An access control that, when enabled, restricts the ability to access datasets to users who are not the creator or owner of them. |