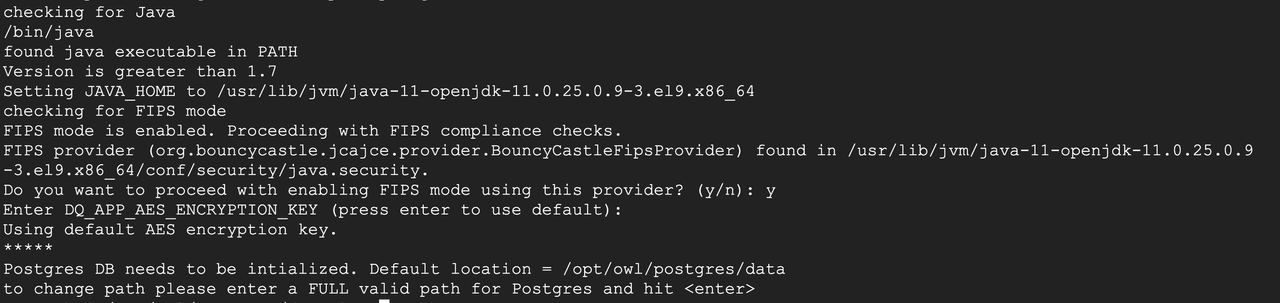
Federal Information Processing Standards (FIPS) are the standards by which many federal and private sector organizations secure their computer systems. Support for FIPS-compliant algorithms in Data Quality & Observability Classic can be configured upon installation through the environment variables in the table below.
The OS environment variable export DQ_APP_FIPS_ENABLED=true is set in the setup.sh, owlmanage.sh, and owl-env.sh files, while all other optional environment variables are set in the owl-env.sh. While all environment variables are optional, if you do not set them, they will default to the out-of-the-box Bouncy Castle configurations.
| Environment variable | Description |
|---|---|
export DQ_APP_FIPS_ENABLED=true
|
Optional. Enables or disables FIPS-compliant algorithms. This must be enabled in the setup.sh and owlmanage.sh file upon the installation of Data Quality & Observability Classic. Default is false. |
export DQ_APP_AES_ENCRYPTION_KEY=<key-string>
|
Optional. Only required when using your own Java security provider, algorithm, and encryption key. Enter the key for AES encryption from your preferred provider. Defaults to the Collibra DQ AES key. |
export DQ_FIPS_PROVIDER_NAME=<java-provider-class>
|
Optional. Only required when using your own Java security provider, algorithm, and encryption key. Provide your own provider implementation. Defaults to Bouncy Castle, which is supported in Collibra DQ and considered one of the secure and compliant FIPS providers. |
export DQ_FIPS_ALGORITHM=<algorithm>
|
Optional. Only required when using your own Java security provider, algorithm, and encryption key. Provide an algorithm supported by your FIPS provider. Defaults to password-based AES 128 encryption algorithm complaint with FIPS. |
Steps
- Before installing Data Quality & Observability Classic, ensure that the entry org.bouncycastle.jcajce.provider.BouncyCastleFipsProvider is set as the security provider in $JAVA_HOME/conf/security/java.security.
- Optionally, set the OS environment variable
export DQ_APP_FIPS_ENABLED=truein the setup.sh and owlmanage.sh files. - Follow the standard Standalone Installation steps.
- Sign in to Data Quality & Observability Classic.
- On the Collibra DQ home page, hover your pointer over
 Settings and select Admin Console.
Settings and select Admin Console.
The Admin Console opens. - Click Agent Configuration.
The Agent Configuration page opens. - In the Actions column, click
to edit your agent.
The Edit Agent modal appears. - In the Free Form (Appended) field, enter the following configuration and ensure that the Bouncy Castle FIPS JAR file, such as bc-fips-x.jar, is included in the directory.
- Restart the DQ web application and DQ agent services.
Example security.provider.13=org.bouncycastle.jcajce.provider.BouncyCastleFipsProvider
-addlib $OWL_HOME/bin/external/Example of environment variables when using the default Bouncy Castle FIPS provider and Collibra DQ values
export DQ_APP_FIPS_ENABLED=true
export DBPASSWORD="String to Encrypt"
# If successful, the following command will return encrypted string
java -cp dq-core.jar:bc-fips-1.0.2.5.jar com.owl.core.security.SecurityManager -encryptString $DBPASSWORD