Important While this method is supported, we recommend using the externally managed JWTs method instead.
This method calls the IdP to retrieve the access_token itself. Data Quality & Observability Classic has an /oath/signin endpoint, which accepts username, password, iss (tenantname) parameters. Data Quality & Observability Classic sends these inputs to the IdP to retrieve an access_token, which Data Quality & Observability Classic then uses to extract the information it needs to create its own token.
Steps
-
Sign in to Data Quality & Observability Classic and click
in the left navigation pane.
- Click Admin Console.
- Click Configuration Settings, then click Application Config. The Application Configuration Settings page opens.
- Set the SSO_API setting to TRUE.
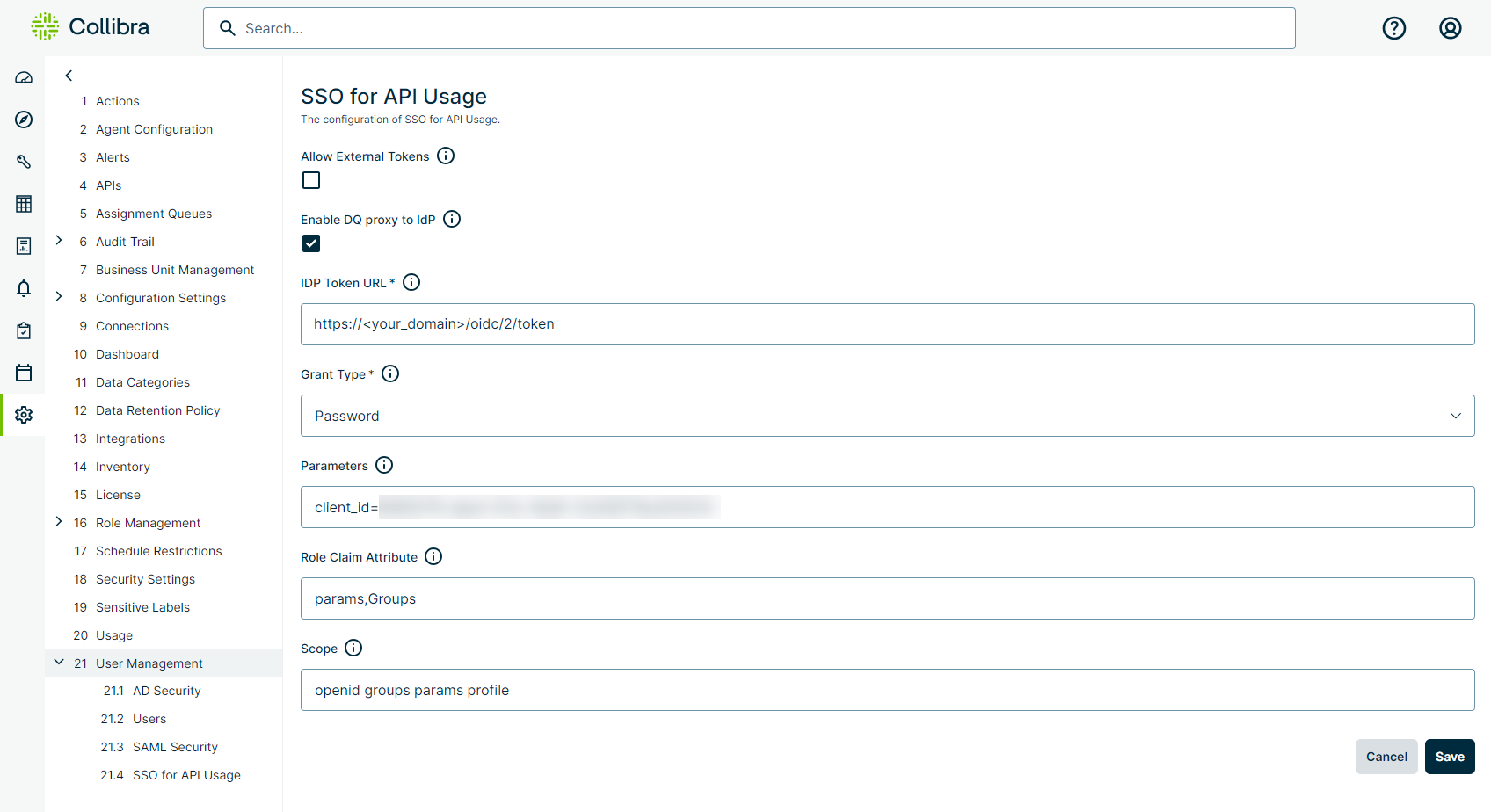
- From the Admin Console treeview menu, click User Management, then API for SSO Usage. The SSO for API Usage page opens.
- Select the Enable DQ Proxy to IdP option.
- Enter the required information.
-
Click Save.
| Field | Description |
|---|---|
| Enable DQ proxy to IdP | Enables SSO for APIs. |
| IdP Token URL |
The token endpoint URL of the identity provider (IdP). Example https://<your_domain>/oidc/2/token |
| Grant Type |
The grant type used for authentication. Select Password. |
| Parameters |
Static query parameters that are appended to the call to the IdP. This is typically found in the URL of the IdP and is specific to the IdP implementation. Example client_id=012345a6-abc1-012a-0ab1-01a23b45cd6789012 |
| Role Claim Attribute |
Attributes in the claims array from the access_token that define where DQ roles and user groups should be mapped. Example params,Groups |
| Scope |
Optional. IdP-specific properties that define the scope of what is returned in the access_token from the OAuth or OIDC request. Example openid groups params profile |
Available global configurations
| owl-env.sh property | Description | Default value |
|---|---|---|
export SECURITY_OAUTH_USECLIENTAUTHORIZATIONHEADER=<value>
|
This is the useClientAuthorizationHeader IdP value. When set to TRUE, this configuration attempts to use clientID and clientSecret to build an authorization header for the IdP request. |
FALSE
|
export SECURITY_OAUTH_CLIENTID=<value>
|
This is the clientID IdP value, which Data Quality & Observability Classic uses to build the authorization header when useClientAuthorizationHeader is enabled. | N/A |
export SECURITY_OAUTH_CLIENTSECRET=<value>
|
This is the clientSecret IdP value, which Data Quality & Observability Classic uses to build the authorization header when useClientAuthorizationHeader is enabled. | N/A |
export SECURITY_OAUTH_FALLBACK_ROLES_IDTOKEN=<value>
|
When set to |
FALSE
|
| Web ConfigMap property | Description | Default value |
|---|---|---|
SECURITY_OAUTH_USECLIENTAUTHORIZATIONHEADER: <value>
|
This is the useClientAuthorizationHeader IdP value. When set to TRUE, this configuration attempts to use clientID and clientSecret to build an authorization header for the IdP request. |
FALSE
|
SECURITY_OAUTH_CLIENTID: <value>
|
This is the clientID IdP value, which Data Quality & Observability Classic uses to build the authorization header when useClientAuthorizationHeader is enabled. | N/A |
SECURITY_OAUTH_CLIENTSECRET: <value>
|
This is the clientSecret IdP value, which Data Quality & Observability Classic uses to build the authorization header when useClientAuthorizationHeader is enabled. | N/A |
SECURITY_OAUTH_FALLBACK_ROLES_IDTOKEN: <value>
|
When set to |
FALSE
|