To fill out your personal information assets with the necessary relations and attributes, your Privacy team has to first create a data classification policy and related standards, data categories, and data attributes. Your Governance team can then map these privacy policy-defining assets to the physical data layer, meaning your System, Table, and Column assets, to inherit the sensitivity characteristics, as defined by your Privacy team.
The following table describes the four privacy policy-defining asset types that are the focus of your Privacy team.
| Asset type | |
|---|---|
| Policy |
A statement of intent that is set by a council and is implemented by a set of standards. In this context, the policy determines how personal information across the organization is classified. Helps an organization determine the minimum privacy and risk controls, to mitigate privacy risk. |
| Standard |
Standards classify data based on their level of sensitivity and organizational impact, were the data disclosed, altered, or destroyed without authorization. They are mandatory actions or rules that help to enforce and support policies. Examples:
|
| Data Category |
A classification of personal data elements that is managed by the Privacy team. Examples:
|
| Data Attribute |
A specification that defines a property of a data asset. For example, the data category Payment Card Information might contain, in part, the following data attributes:
|
Note The images in this example show the classic user interface. You can still refer to them to understand the concept.
Suppose that your Privacy team has decided to distinguish all data across the organization with one of three "labels," or standards, based on different levels of sensitivity.
With such decisions made, a Privacy Steward creates:
- A Policy asset named Data Classification Policy, to fully describe all such decisions and details.
- Three Standard assets: one named Public, to distinguish your least sensitive data; one named Private; and one named Restricted, to distinguish your most sensitive data.
- A relation that groups the three Standard assets under the Data Classification Policy asset.
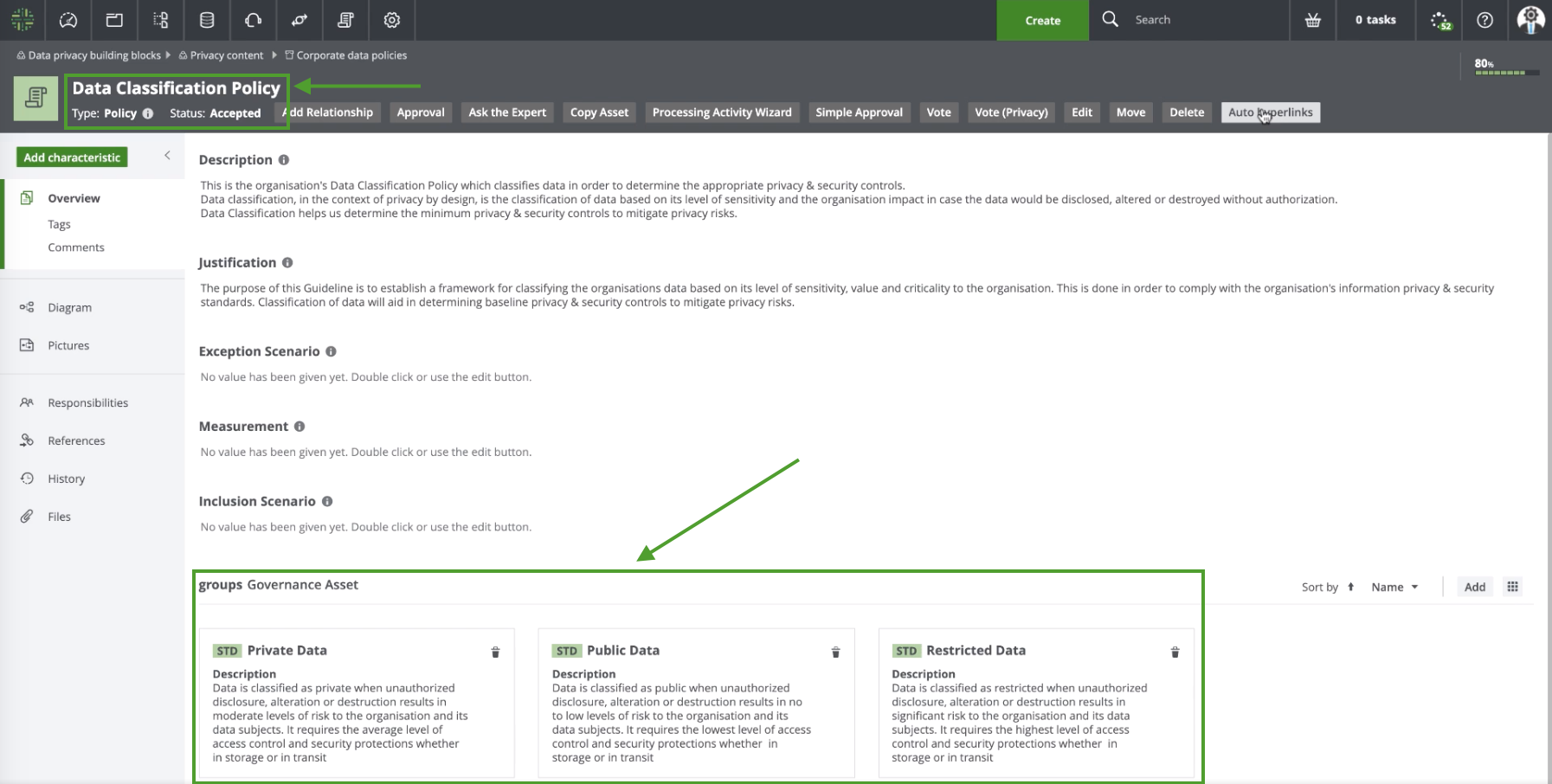
The Privacy steward then creates:
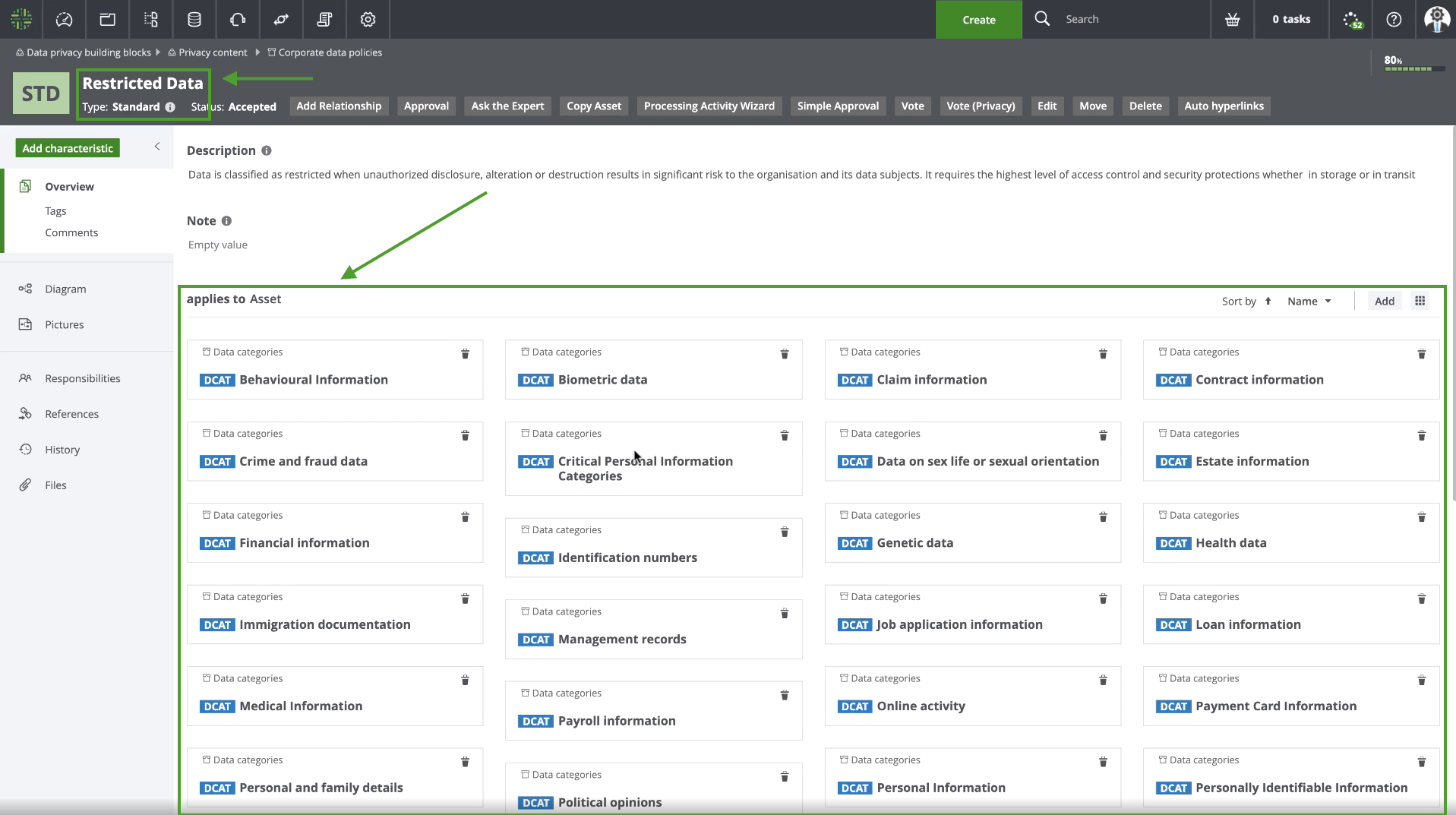
- Data Category assets, which help you to segregate all data across your organization according to subject matter.
- Relations, such that one of the Standards applies to each of the Data Category assets.
The following image shows which data categories have been deemed restricted.
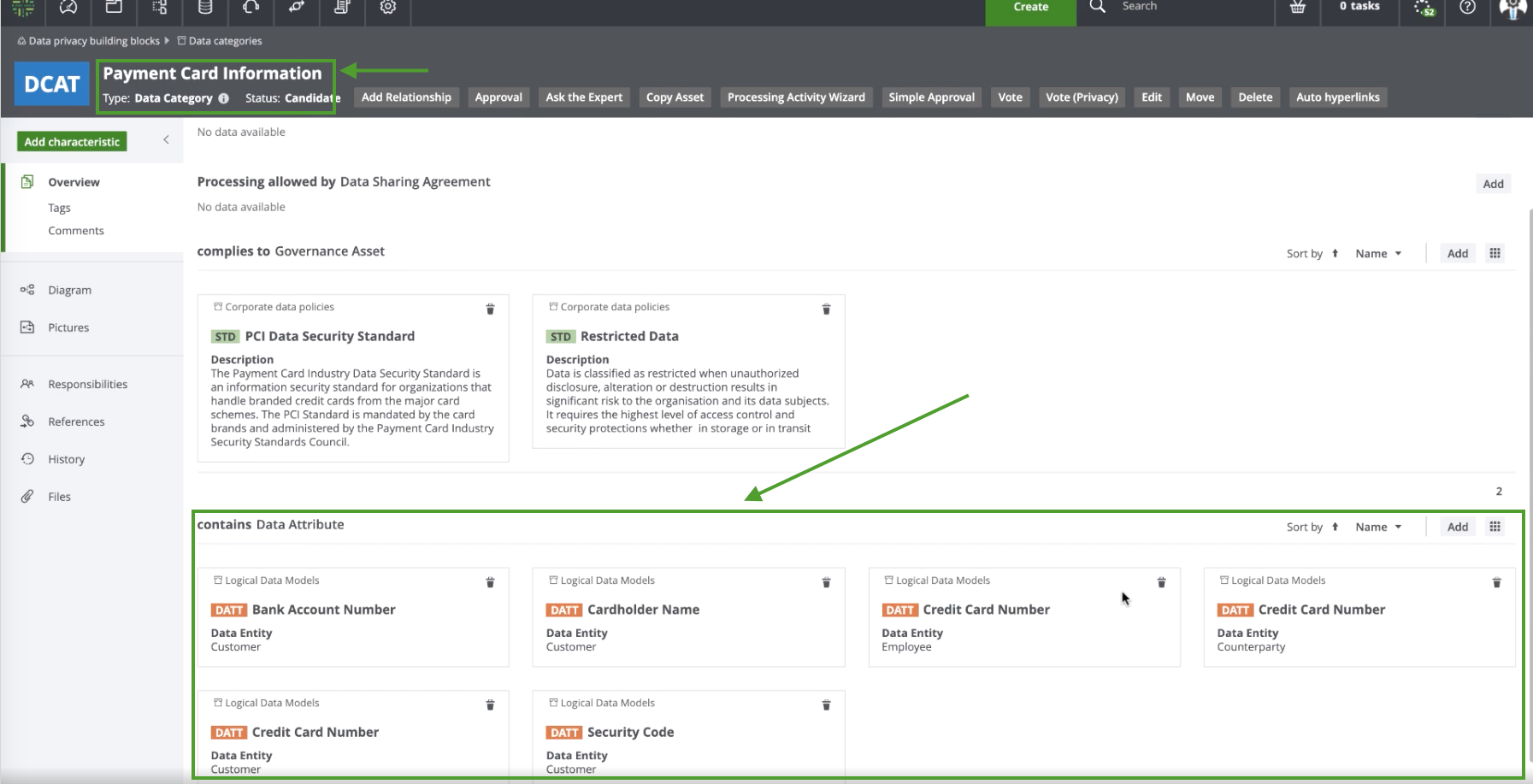
Each Data Category asset, for example, Payment Card Information, contains data attributes that are specific to payment card information, for example, Cardholder Name and Credit Card Number. The following image shows the relations between the Data Category asset and the Data Attribute assets.
The Governance team can then map these privacy policy-defining assets to the physical data layer, meaning your systems, tables, and columns.
Security attribute for System assets
Your Governance team will map your Table assets and Column assets to the System assets that produce and consume data, so that you can quickly see in which systems PI is being used. Your InfoSec Stewards can add a security level attribute to the System assets, so that you can see whether or not your systems have the required level of security (this is an attribute of the system asset).
View a diagram of the mapping
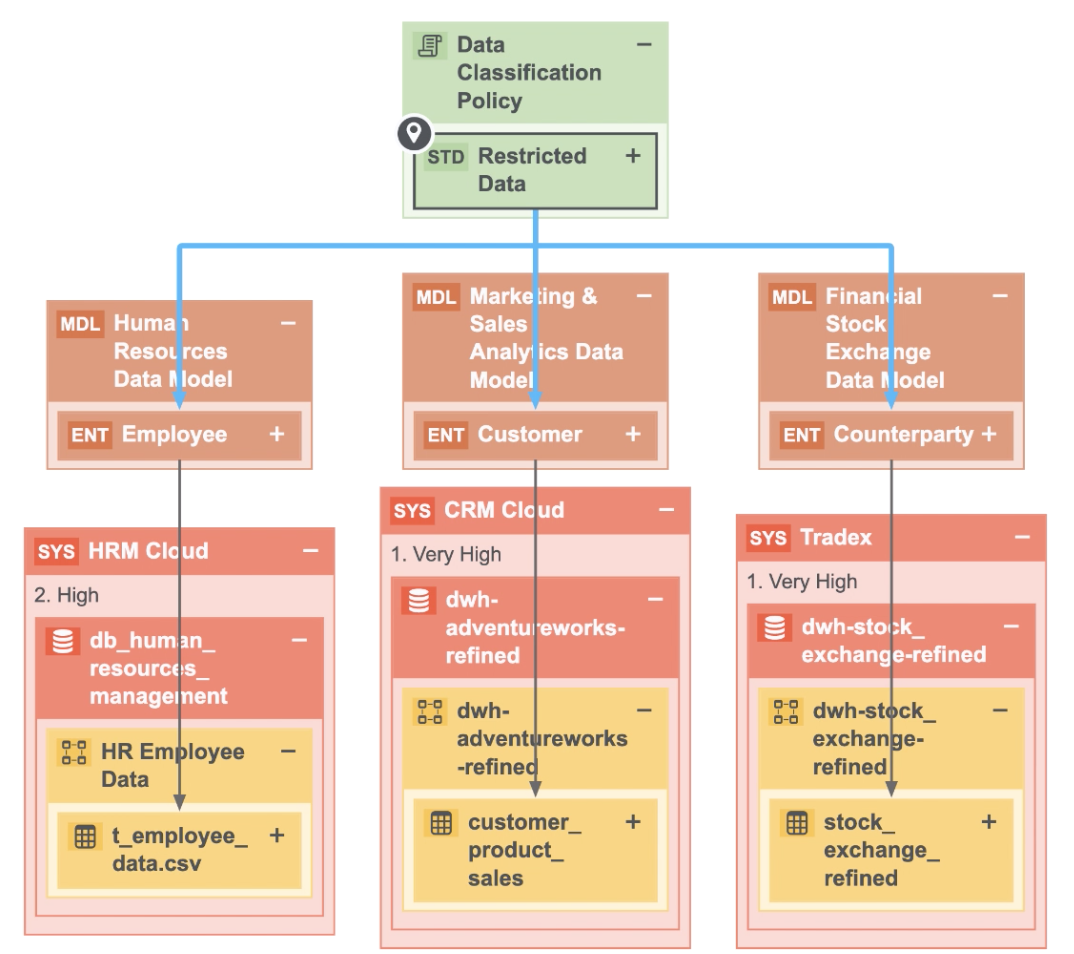
The following image shows a lineage diagram after mapping privacy policy-defining assets to the physical data layer.
Here we can identify:
- All the systems in which restricted data is stored, specifically HRM Cloud, CRM Cloud, and Tradex.
- Whose restricted data is being stored, specifically Employee, Customer, and Counterparty data.
- The security level of each system, for example, "Very High" for the System assets CRM Cloud and Tradex.