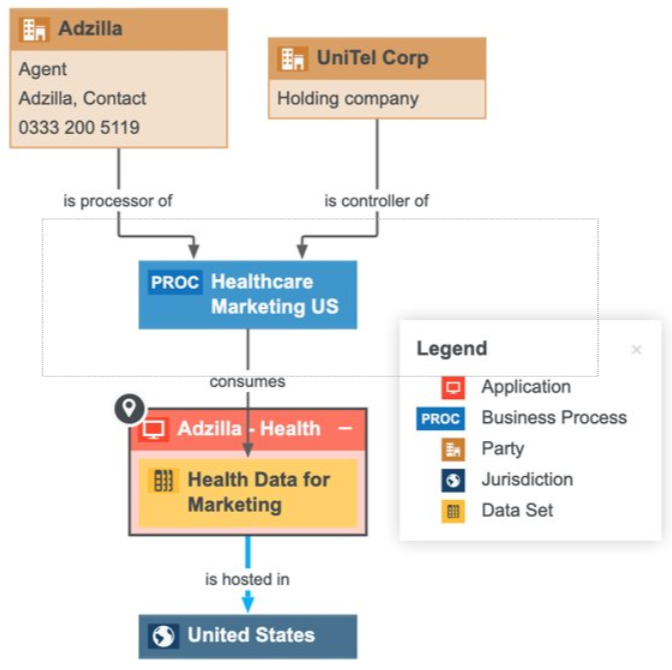
It's important to maintain an inventory of the applications, across your organization, that consume and produce data. With a complete application inventory, you can map your applications to the personal data consumed and processed by each application, and set the security level for each application. With additional mapping, you can identify:
- In which Technology Assets your personal data resides, and the security level of these assets.
- By which applications your personal data is being consumed and produced.
- In which jurisdiction your personal data is being hosted.
- Which risks and security issues could impact your applications.
Tip
- Identify the applications across your organization that consume or produce personal information.
- Create new Application assets as necessary.
- Analyze the out-of-the-box attributes configured in the global assignment for the Application asset type, and add any attributes you might want.Note Be sure to add the Security Level attribute to the Technology Asset global assignment. This attribute is essential for identifying the security level of the Technology Assets that host personal data and the Application assets that consume or produce personal information, those that could be potentially impacted by risks, and so on.