If you want to ingest data and profile that data, you can use a Jobserver service, often referred to as Jobserver. If the Data Governance Center service and Jobserver service are in the same network segment, you can use the insecure HTTP protocol with no authentication. However, it is highly recommended to configure a secure communication.
In the following schema, you can see how the communication is established for mutual authentication between the two services. This authentication level is the recommended level whenever both services are in a different network segment, for example when you have a cloud-based Collibra Platform environment and an on-premises Jobserver.
If there is a reverse proxy server between these services, see Mutual authentication with a reverse proxy server.
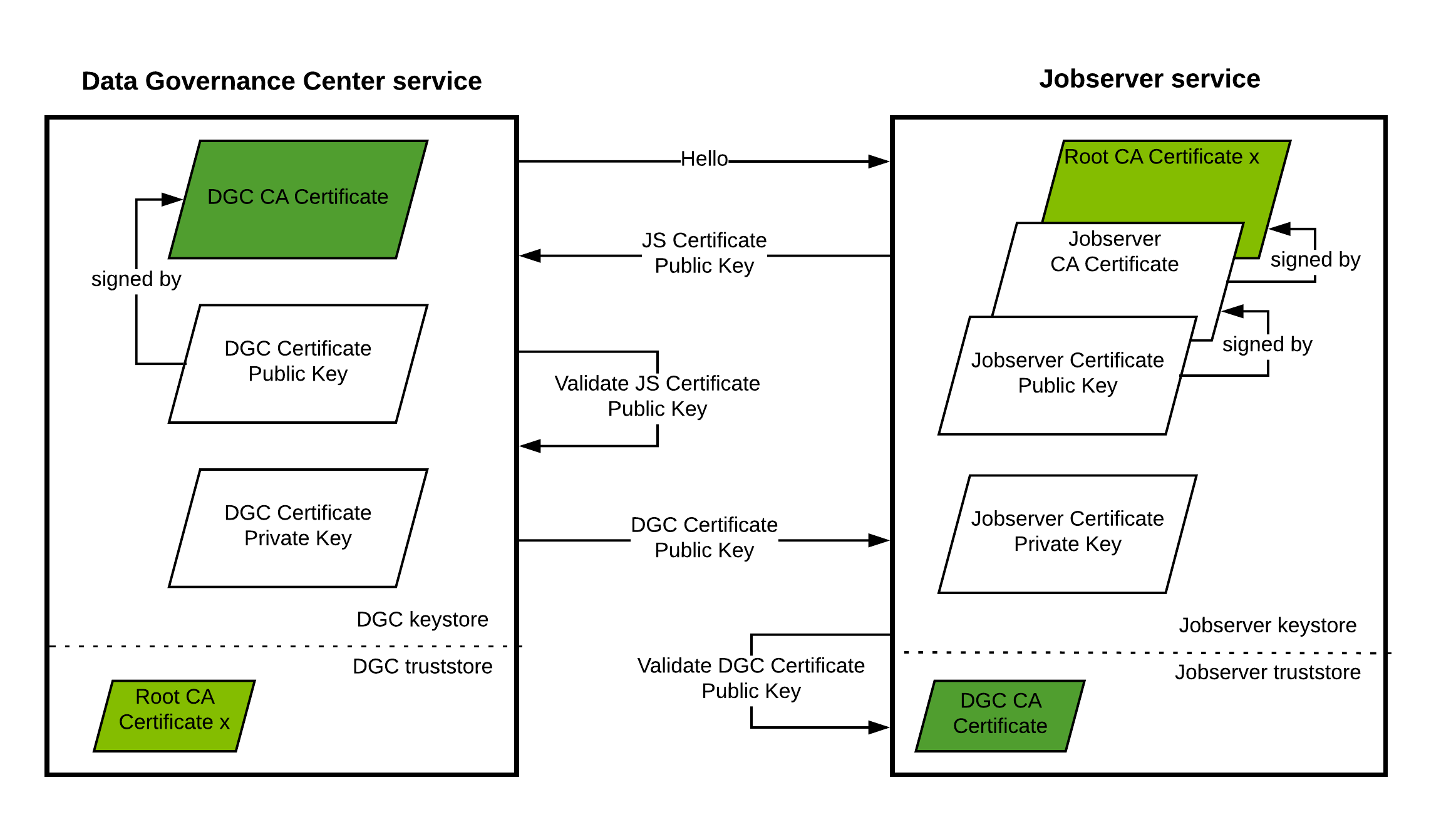
|
Step |
Description |
|---|---|
| Hello | DGC service initiates the communication to the Jobserver service by sending a Hello message. |
| JS Certificate Public Key |
The Jobserver service sends its public key to the DGC service. The DGC service can then authenticate the Jobserver service. |
| Validate JS Certificate Public Key |
The DGC service validates the received public key with the Jobserver's CA certificate. This means that the DGC service has the Jobserver's CA certificate in its truststore. |
| DGC Certificate Public Key |
The DGC service sends its public key to the Jobserver service. The Jobserver service can then authenticate the DGC service. |
| Validate DGC Certificate Public Key |
The Jobserver service validates the received public key with the DGC CA certificate. This means that the Jobserver service has the DGC CA certificate in its truststore. |
If all these steps are completed successfully, then both services are 100% sure that they are communicating with the counterparty that they expect.
It is only the DGC service that initiates the communication to the Jobserver service. The communication from a Jobserver to the DGC service is only possible with a reverse proxy.