Working with SAML
SAML or Security Assertion Markup Language is an open standard that allows security credentials to be shared by multiple computers across a network. It describes a framework that allows one computer to perform some security functions on behalf of one or more other computers.
For more information, see the website of the OASIS Security Services (SAML) Technical Committee.
Terminology
| Term | Explanation |
|---|---|
| SP | The Service Provider of the SAML integration. In this case, the SP is Collibra Platform. |
| IDP |
The Identity Provider of the SAML integration. In this case , the IDP depends on your company. Examples of IDPs: Microsoft's Active Directory (if the federation services are installed), PingFederate, SiteMinder, Okta, OneSign... |
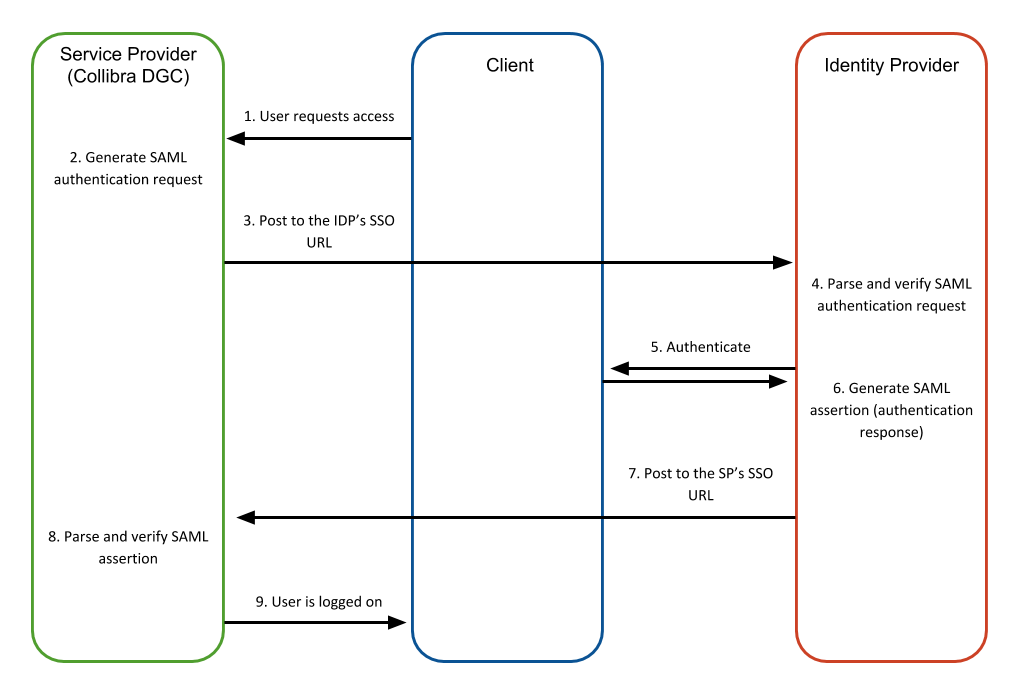
| SP-initiated sign-on |
A type of sign-on that starts from the SP (Collibra). In this flow, the SP asks the IDP to authenticate the current user, using a SAML request. The IDP then returns a SAML response. This SAML response contains the assertion of the user currently visiting the SP. That assertion contains the properly configured attributes of the user that is requested. Note If the assertion's SubjectConfirmationData element contains the Address attribute, ensure that the value is a URL. This value indicates the expected network address of the client.
|
|
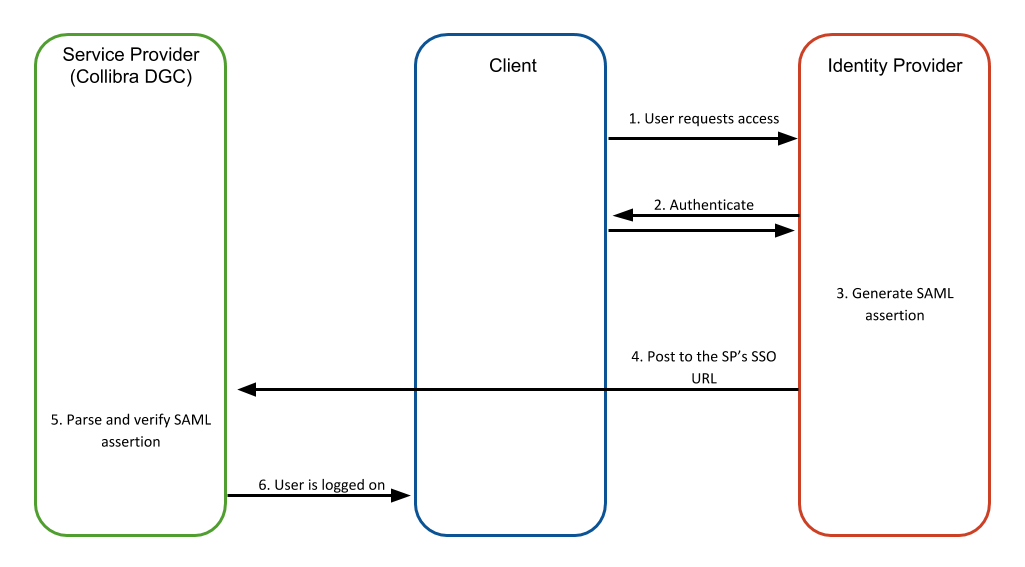
IDP-initiated sign-on |
A type of sign-on that starts from the IDP portal towards the SP. This flow skips the SAML request sent in the SP-initiated flow, but still sends the SAML Response containing an assertion containing the properly configured attributes of the user that is requested.
|
Supported SAML 2.0 profile
Although SAML 2.0 is a clear standard, it is too large to support in its entirety. The designers of the SAML standard also realized this and that's why they developed SAML Profiles. These profiles are defined in the SAML 2.0 specification's section.
The purpose of SAML profiles is to allow both IDP and SP to decide to only support a subset in the SAML protocol that is applicable to them, in their situation.
Collibra supports the Web Browser SSO Profile.
How does Collibra implement SAML?
Even though the web browser profile is properly defined in the standard's profile section, there are a lot of optional features, but not all of them are implemented. This section explains what is implemented and what not.
The profile defines that metadata may be used to build trust between SP and IDP. Collibra has chosen to enforce this, so the only way to integrate your IDP with Collibra is for the IDP to provide the metadata to Collibra. This can be done by either uploading a SAML metadata file, or by providing a public URL that contains the metadata.
The profile explains that signing and/or encryption of SAML requests and responses can be used and that Collibra expects the IDP to perform the signing and/or encryption. Since the communication between SP and IDP is always supposed to happen in the context of an HTTPS connection, encryption is not performed. The transport layer takes care of that.
By default, SAML requests are not signed, but you can enable signed requests. SAML responses always have to be signed because the response has to come from the correct IDP.
The validUntil property in the SAML metadata
The SAML metadata may contain a validUntil attribute. This optional attribute indicates the expiration time of the metadata contained in the element, as well as its child elements.
The "valid until" field is taken into account by Collibra. SAML will stop working either when the validity period has expired or when the content in the metadata file is no longer valid.
Steps for integrating SAML in Collibra
| Step | Task | Description |
|---|---|---|
| 1 | Bring in the IDP's SAML metadata in Collibra Console |
Collibra needs the metadata of your IDP. You can bring in the metadata in two ways:
|
|
2 |
Configure DGC |
Configure the environment settings for SSO SAML with attributes or SSO SAML with LDAP. We strongly recommend that you enable Sign authentication requests. If you do not enable Sign authentication requests, Collibra's outgoing requests are not signed. If your IDP demands that all requests are signed, the unsigned requests from Collibra will be ignored. |
| 3 | Restart Collibra |
Stop and start the affected environment. This will generate a key pair, which is required to sign authentication requests. |
|
4 |
Bring in Collibra's SAML metadata in your IDP |
Your IDP needs the metadata of Collibra. Your IDP team should help with this. To obtain the metadata file from Collibra and import it in your IDP, sign in and download the metadata file from |
| 5 | Configure your IDP | You IDP may require further configuration. Your IDP team should help with or perform the complete configuration. |